Now we need to create the developer assume role policy.
To check if system:unauthenticated group has system:discovery permissions on your cluster run the following command: To check if system:unauthenticated group has system:basic-user permission on your cluster run the following command: If system:unauthenticated group is bound to system:discovery and/or system:basic-user ClusterRoles on your cluster, you should disassociate these roles from system:unauthenticated group. For those without single sign-on (SSO), leveraging IAM Users and Groups is the recommended way of handling authentication. Authentication involves the verification of a identity whereas authorization governs the actions that can be performed by AWS resources. The GTA market is VERY demanding and one mistake can lose that perfect pad. There are a few options here, depending on how you deployed your cluster: Terraform is a software based infrastructure as code tool developed by Hashicorp that we highly recommend for all projects to help retain clear and concise definitions for cloud infrastructure. Azure AD. There may be some legitimate reasons to enable anonymous access on specific APIs. RBAC permissions can be assigned to this IAM role in two ways : 1. In all cases, the aws-iam-authenticator configuration snippets will represent part of the Kubernetes ConfigMap it reads config from. arn:aws:iam::111122223333:role/eksctl-my-cluster-nodegroup-standard-wo-NodeInstanceRole-1WP3NUE3O6UCF, Self-built proxy system for GitHub repositories, NPM packages, and WordPress themes and plugins, A Golang library that generates a random adjective and Ubisoft game given a UUID, Snob - A simple CLI that fetches movies and TV shows info, written in Go, Gimana caranya buat sistem checkout yang batal otomatis, Canonical location of the Dragonfly API definition, Live stock and crypto tickers for your discord server, Hyperledger Fabric Smart Contracts and Application for Edge Node selection, That Lambda layer uses a wrapper script to fetch information from Secrets Manager and create environmental variables, Golang with Zig (used as cross-compilation toolchain and more! mfa authentication prwatech Let's assume the IAM role eks-developer with session name containing @ : Now Cloudwatch logs would have session name printed as eks-developer:my-developer-session-123456789. tenable aws authentication This way you can manage their permissions via a role and role-binding within Kubernetes. and only accessible to Shardul Srivastava. authenticator If you need to grant an IAM user access to an EKS cluster, create an entry in the aws-auth ConfigMap for that user that maps to a specific Kubernetes RBAC group. 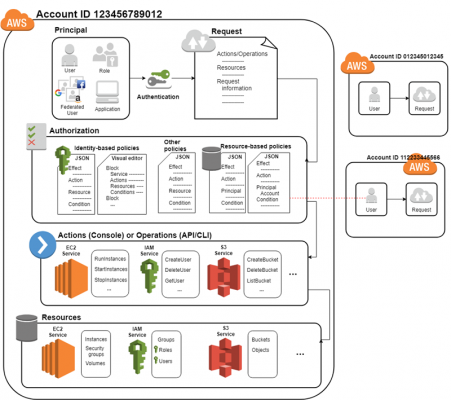 For a complete listing of the SDKs that currently support IRSA, see https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-minimum-sdk.html.
For a complete listing of the SDKs that currently support IRSA, see https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-minimum-sdk.html.  If you update the securityContext for your container to include fsgroup=65534 [Nobody] it will allow the container to read the token. If you have an application that is using an older version of the AWS SDK that doesn't support IRSA, and you want the pod to inherit the role assigned to the instance, consider using Kubernetes network policies to selectively allow access EC2 metadata. eks jumpstart terraform If you created your cluster via eksctl then use the eksctl create iamidentitymapping cli function.
If you update the securityContext for your container to include fsgroup=65534 [Nobody] it will allow the container to read the token. If you have an application that is using an older version of the AWS SDK that doesn't support IRSA, and you want the pod to inherit the role assigned to the instance, consider using Kubernetes network policies to selectively allow access EC2 metadata. eks jumpstart terraform If you created your cluster via eksctl then use the eksctl create iamidentitymapping cli function.
An improperly formatted aws-auth ConfigMap may cause you to lose access to the cluster. It works by leveraging a Kubernetes feature known as Service Account Token Volume Projection. Built on Forem the open source software that powers DEV and other inclusive communities. While IRSA is the preferred way to assign an AWS "identity" to a pod, it requires that you include recent version of the AWS SDKs in your application. By default when you provision an EKS cluster, the API cluster endpoint is set to public, i.e. code of conduct because it is harassing, offensive or spammy. You can see an example terraform setup using this method inside the repository below: https://github.com/terraform-aws-modules/terraform-aws-eks/tree/v16.0.1/examples/basic. Note: If you want session name in raw format, you can use templated variable {{SessionNameRaw}} instead. AKS Heres the scenario: You want to deploy a fancy new AWS Elastic Kubernetes Service, or EKS cluster as its commonly called, running the latest version of Kubernetes. The value of runAsUser is arbitrary value. Again, make sure you change the ACCOUNT_ID variable to your AWS account id. appsync aws methods authentication multiple rfc figure RBAC permissions with Kubernetes Groups. cognito authentication amplify iam serverless benutzer groupes If the session name consists of @, it would be replaced with -. Prior to Kubernetes 1.24, Kubernetes would automatically create a secret for each a service account. This access cannot be removed and is not managed through the aws-auth ConfigMap. That said, if your corporate security policy mandates that you restrict access to the API from the Internet or prevents you from routing traffic outside the cluster VPC, you can: When you create an Amazon EKS cluster, the IAM entity user or role, such as afederated userthat creates the cluster, is automatically grantedsystem:masterspermissions in the cluster's RBAC configuration.
Per AWSs documentation, "an IAM role is similar to an IAM user, in that it is an AWS identity with permission policies that determine what the identity can and cannot do in AWS. for the EKS cluster. A better alternative would be to use aws-iam-authenticator to map this to a new Kubernetes group that you can attach specific RBAC bindings to: With that group, you could create RBAC Bindings with RBAC Manager that would allow you to specify access specifically for that group. Go ahead and create another JSON file named eks-developer-assume-role-policy.json with the following. The example aws-iam-authenticator configuration below uses a bit of a shortcut to use a group that already is bound to a cluster-admin role (system:masters). No matter their experience level they agree GTAHomeGuy is THE only choice. Note: Do not add the developer role to any pre-created groups in Kubernetes. Here is what you can do to flag aws-builders: aws-builders consistently posts content that violates DEV Community's If you like the above approach, but would prefer to just map all IAM users automatically to RBAC users, there's an aws-iam-authenticator configuration (opens new window) option for that as well: With this approach, all IAM users are mapped to Kubernetes users with the full ARN as the username. This signed token allows the Pod to call the AWS APIs associated IAM role. Although AWS doesn't endorse or condone the use of these solutions, they are frequently used by the community at large to achieve similar results as IRSA. centralised permissioned properly See. This library provides a variety of ways of mapping IAM roles and users to Kubernetes groups and users. From Amazon's documentation, IAM users represent the person or service who uses the IAM user to interact with AWS. worker kubernetes sayem This role should not be used to perform routine actions on the cluster, and instead additional users should be granted access to the cluster through the aws-auth ConfigMap for this purpose. As an Amazon Associate, we earn from qualifying purchases. 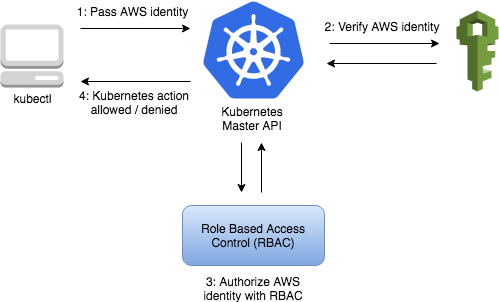 This will be easier to maintain, especially as the number of users that require access grows.
This will be easier to maintain, especially as the number of users that require access grows.  A downside to this approach is that authorization configuration ends up getting split between AWS IAM Roles assigned to users and RBAC bindings. Jenkins, you will need to create a secret of type kubernetes.io/service-account-token along with an annotation that references the service account such as metadata.annotations.kubernetes.io/service-account.name:
A downside to this approach is that authorization configuration ends up getting split between AWS IAM Roles assigned to users and RBAC bindings. Jenkins, you will need to create a secret of type kubernetes.io/service-account-token along with an annotation that references the service account such as metadata.annotations.kubernetes.io/service-account.name:
As per EKS docs: EKS uses IAM permissions for authentication of valid entities such IAM users or roles. Allows super-user access to perform any action on any resource.
For further information about IRSA, see https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-technical-overview.html. In order to do this, we need to create a role within the namespace, so that the user will have permissions. The AWS SDKs are responsible for reloading the token when it rotates. nps aws authentication First delete the earlier ClusterRoleBinding eks-developer-user-cluster-role-binding : As soon as we delete the ClusterRolebinding, eks-developer IAM role won't be able to list the pods, let's check the access by assuming the eks-developer IAM role : Create a ClusterRoleBinding to bind Kubernetes Group developer to cluster role eks-developer-cluster-role: Add Kubernetes Group developer to IAM role mapping of eks-developer in aws-auth and include the session name in username using templated variable {{SessionName}}: this would create an entry under mapRoles section in aws-auth configmap as: Check the Cloudwatch authenticator logs for the authenticated user assuming eks-developer IAM role and we can see that this time session name is appended to the username in logs: time="2021-09-13T17:57:46Z" level=info msg="access granted" arn="arn:aws:iam::0175XXXXXXXX:role/eks-developer" client="127.0.0.1:48520" groups="[developer]" method=POST path=/authenticate sts=sts.us-east-1.amazonaws.com uid="heptio-authenticator-aws:0175XXXXXXXX:AROAQIFUWO66PDOXKSLMQ" username="eks-developer:eks-developer-session". ConfigMap.
One important point before we get started, make sure to deploy your cluster with a role that others can assume. Creating an efficient process for storing application logs is critical for cybersecurity and compliance. The token has a time to live (TTL) of 15 minutes after which a new token will need to be generated. To start with the basics, IAM is defined as Identity and Access Management within AWS. See https://eksctl.io/usage/iamserviceaccounts/ for further information. At present, the aws-node daemonset is configured to use a role assigned to the EC2 instances to assign IPs to pods. In the following example, all processes within the Pod will run under the user ID specified in the runAsUser field. Future plans, financial benefits and timing can be huge factors in approach. Who requires access is likely to change over time. With you every step of your journey. First, start by creating two IAM roles named eks-admin-role and eks-developer-role with the following CLI commands: aws iam create-role --role-name eks-admin-role --output text --query 'Role.Arn', aws iam create-role --role-name eks-developer-role --output text --query 'Role.Arn'. Additional ideas can be found in this article from NCC Group. If you employ a blue/green approach to cluster upgrades instead of performing an in-place cluster upgrade, you will need to update the trust policy of each of the IRSA IAM roles with the OIDC endpoint of the new cluster. The rules governing the actions that a resource is allowed to perform are expressed as IAM policies. A blue/green cluster upgrade is where you create a cluster running a newer version of Kubernetes alongside the old cluster and use a load balancer or a service mesh to seamlessly shift traffic from services running on the old cluster to the new cluster. time="2021-09-14T17:50:25Z" level=info msg="access granted" arn="arn:aws:iam::017558828988:role/eks-developer" client="127.0.0.1:57794" groups="[developer]" method=POST path=/authenticate sts=sts.us-east-1.amazonaws.com uid="heptio-authenticator-aws:017558828988:AROAQIFUWO66PDOXKSLMQ" username="eks-developer:my-develper-session-123456789". Let's create two IAM roles eks-admin and eks-dev and assume the eks-admin role to create a cluster with one node group: Once created, this cluster would have one NodeGroup and the IAM role associated with this node group would be added to the aws-auth configmap. At times, you may need to grant an exception for applications that have to consume the Kubernetes API from outside the cluster, e.g. If you use EKS then you have found yourself in a situation where a user can't access the cluster despite having all the IAM permissions and gets an Unauthorized message like Eddie here. In EKS, IAM permissions are only used to check if the user has valid IAM credentials and permissions to run any command using kubectl such as kubectl get pods is managed by Kubernetes API that uses RBAC to control the access. Here's the command line inputs for the groups: aws iam put-group-policy --group-name eks-admin-group --policy-name eks-admin-assume-role-policy, aws iam put-group-policy --group-name eks-developer-group --policy-name eks-developer-assume-role-policy. # Allow user to get, list of watch the pods. If you're using an IAM role, the actual users who assume that role aren't recorded and can't be audited. For an exhaustive view into IAM users and groups, check out the full documentation from Amazon. Secrets created in this way do not expire. We can also verify the access granted to the users by checking the authenticator logs in Cloudwatch: time="2021-09-13T16:29:14Z" level=info msg="access granted" arn="arn:aws:iam::01755xxxxx:role/eks-developer" client="127.0.0.1:50410" groups="[]" method=POST path=/authenticate sts=sts.us-east-1.amazonaws.com uid="heptio-authenticator-aws:01755xxxxx:AROAQIFUWO66PDOXKSLMQ" username=eks-developer. With EKS, this is included by default, and it's fairly straightforward to setup with Kops (opens new window) or other methods of cluster provisioning. aws authentication ec2 instances factor IAM Users and Roles, and Kubernetes RBAC groups. After validating the token's signature, IAM exchanges the Kubernetes issued token for a temporary AWS role credential. Hows that going to work?". You are now ready to run commands against the cluster.
When you run a container as a non-root user, it prevents the container from reading the IRSA service account token because the token is assigned 0600 [root] permissions by default. react amplify While this allows them to read the web identity token file, running a container as root is not considered a best practice. The eksctl CLI includes a command for adding identity mappings to the aws-auth Save the following JSON to a file in your current directory and name it eks-admin-assume-role-policy.json and change the relative variables to match your AWS account number. cognito ressourcen backend apis zugreifen serverseitige The blocks are effectively a whitelisted set of public IP addresses that are allowed to access the cluster endpoint. immutable instances deployed Once unpublished, this post will become invisible to the public We offer a variety of DevOps Consulting Services, and we're always happy to help companies of any size with their DevOps strategy. This blog post will walk you through how to get authentication working correctly from the beginning! Decoding the service account token in that directory will reveal the following metadata: The default service account has the following permissions to the Kubernetes API. A service account is a special type of object that allows you to assign a Kubernetes RBAC role to a pod.
Lastly, if you created your cluster via the AWS Console/UI, then use the kubectl CLI to edit the config map via vim. Bearer Tokens, X.509 certificates, OIDC, etc. eks authentication iam aws cluster user process manage autoscaling limited access medium kubernetes users role managed EKS adds support IMDSv2 by enabling both v1 and v2 and changing the hop limit to 2 on nodes provisioned by eksctl or with the official CloudFormation templates. With the above config you could specify RBAC Bindings with the following RBAC Definition: Although we no longer need to understand which AWS IAM users can assume specific IAM roles. Are you sure you want to hide this comment? Check the contents of aws-auth configMap : By default, only IAM Role that created the cluster would have access to the cluster, any other IAM Role has to be added separately added in aws-auth. Create a ClusterRoleBinding to bind Kubernetes user dev-user to the developer-cluster-role: Map IAM user arn:aws:iam::