For instance, a new software version is not compatible with your data formator a new operating system does not support your software; the media on which data is stored becomesoutdated (e.g. Learn about different measures depending on the kind of security you need: The Netherlands Code of Conduct for Research Integrity (VSNU, 2018)states that research datamust be kept for (at least) 10 years.
data storage management surf nl 
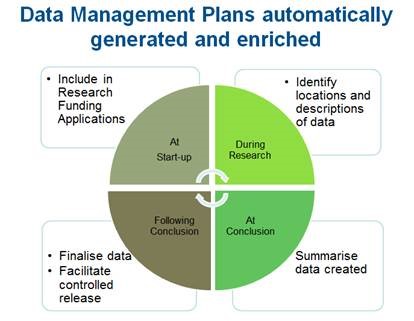 Where possible, only store what you need to keep.
Where possible, only store what you need to keep. 
 By reflecting the research phases in your folder structure, the structure also reflects the different versions of your research data. Take into account the possibilities and limitations of the (storage) system you are working with. with and later for others who will reuse your data. Secure your data files'above. Keep file names as short and relevant as possible. It is better to use the secure tool SURFfilesender, which also uses encryption. Document the choices you make in terms of folder names and folder structure, including all changes in the folder structure and the associated arguments. nwu rdm How close are you to making a final study choice? Document your entire strategy with regard to giving file names. cloud security computing privacy secure research phd student topic why data management figure right As such, it is important that each researcher considers the ramifications of sharing folders and files with others before doing so.
By reflecting the research phases in your folder structure, the structure also reflects the different versions of your research data. Take into account the possibilities and limitations of the (storage) system you are working with. with and later for others who will reuse your data. Secure your data files'above. Keep file names as short and relevant as possible. It is better to use the secure tool SURFfilesender, which also uses encryption. Document the choices you make in terms of folder names and folder structure, including all changes in the folder structure and the associated arguments. nwu rdm How close are you to making a final study choice? Document your entire strategy with regard to giving file names. cloud security computing privacy secure research phd student topic why data management figure right As such, it is important that each researcher considers the ramifications of sharing folders and files with others before doing so.
There are many providers of cloud storage out there and you should check their terms of use before using them for your research data. commvault spectra tape insidehpc and your data (in the form of inventories, descriptions of relationships and manipulations, etc.) This tutorial is part of the online training 'Learn to write your DMP'. All this starts with a good data management policy and the right tools (storage features) which should be compatible and act as a reflection of your effective data management policy. A file name can only hold so much information. Observe the following fixed rules: the same number of digits (001100), fixed notation for dates (YYYY-MM-DD, YYYY-MM or YYYY-YYYY), underscores and hyphens instead of spaces, standard terms (get inspiration from bartoc.org), no special characters and leave file extensions unchanged. For sharing, data should be stored as raw as possible (if usable in that form) along with documentation to help comprehend and reuse it. Storing master copies of digital data on individual desktop or laptop computers is also not recommended.
Periodically check that no unauthorised access takes place and verify who has access to which folders and files. However, you can prevent data loss by following good backup practices. When organising access to your data during the course of your research, you should take into account the nature of the data. For example: Researchers should identify the possible retention period for used data and also potential requirements for retention and disposal and consult the Queensland State Archives University Sector Retention and Disposal Schedule below, Dr Lisa Marlow
a bad batch of discs), The more important the data and the more often they change, the more regularly they need to be backed up. The guidelines for writing such a README.txt file have been established by the 4TU Centre for Research Data. When you need to share your data during research take into account the wishes of rightful claimants to the data (research subjects, co-authors, partners from industry, etc.) However, the most convenient ways to store research data may not always be the most appropriate one. See 'Data description in practice'for more specific guidance and tips or watch this tutorial 'The ins and outs of metadata and data documentation'. kalray Risks also emerge for users if the software required resolving the format is restricted or the developer changes licensing or costed use of that software. complementarity abdessamad data center india gartner spending marginally rise infrastructure cxotoday Personal or sensitive data require a higher level of security than anonymised or non-confidential data. This list may be supplemented by other variables. has services that cover every step of the research data lifecycle? For yourself, for the researchers you work Non-anonymised data may, however, be preserved for historical, statistical or scientific purposes. Depending on your institution, community or ministry/national policies, you may be required to implement long-term data preservation and ensure that your research data is stored in an accessible place for 10 or even more years! There are many issues to consider, and it is recommended researchers should seek early advice from a Research Data Advisor, or the Office of Research Services. It is also the start of your folder structure. A project folder is created per research project in which you can create your own folder structure or make use of a recommended folder structure. Always lock your device when you walk away and never leave your device unattended/unprotected for long periods of time. LabArchives is an industry standard electronic lab notebook availableto all HDR and academic staff to report research. Choosing what to keep and what can be disposed of or deleted is always going to involve a subjective judgement, as nobody knows exactly what information is going to be wanted in the future. Check out below what are the main problems with storing research data incorrectly. storage capacity data fotolia primary If you have made use of data from other parties, you will have to account for them as well. Did you know that the EUDAT Collaborative Data Infrastructure (EUDAT CDI) is important to avoid errors and to interpret data correctly during your research and after your research is completed (validation). The shortcut to the tool can be found via this link, but is of course only accessible if you have registered your research with the functional manager. If you have any questions about this site, please e-mail us directly. patient records); If the work has community or heritage value, research data should be kept permanently at this stage, preferably within a national collection. You may be required by your PI or funder to store your data in a particular place, or you may have more choices available. And apply encryption as an additional security measure. In order to keep an overview in your folder structure, the best approach is to reflect the different phases of your research. Store crucial data in more than one secure location. About 25 characters is a good length for a filename. considerations TheUtrecht University Policy Framework for Research Dataadds that this 10 year periodstarts after you have published your paper based on the data you are preserving. Handle passwords wisely.
Correct storage enables this.
At first glance, storing your research data should not be a difficult task with all the options we have at our disposal; youve got your USBs, external hard disks, cloud drives, or even on websites or their institutional repositories. If your files take up a large amount of space and backing up all of them (or backing them up sufficiently frequently) would be difficult or expensive, you may want to focus on backing up specific key information, programs, algorithms, or documentation that you would need in order to re-create the data in case of data loss.
The research data steward(s) of THUAS can be contacted at researchsupport@hhs.nl, 2022 The Hague University - All rights reserved, Data management (storage and organisation), Guidelines folder structure in Research Drive.
Documenting both your research process (in the form of protocols, methodology descriptions, etc.) You need to consider these carefully and make an informed decision about sharing your folders and files with others. Research data should be readable for machines without the need for specialised or ad hoc algorithms, translators, or mappings, but if your storage system cannot support this, then you may be limiting how far your research data can be used., Moving files from one storage space to another commonly needs to happen whether in research data or even for personal files. Your data management plan is a good place to document your file naming conventions. Arrange with the owners that they store the data and make it available for verification purposes, for at least the obligatory period of storage (ten years). Learn how to select what to keep and how to store it carefully. How do you deal with possible terms of use of the data? Think about the: Documentation (human readable) and metadata (standardised, fixed fields that can take a value, computer readable)both provideinformation about the data at hand. So, how will you keep your data safe for the long term? Find out how to preserve your data and back-ups, and consider how you can get the most from your data, perhaps through re-use and sharing. USB sticks), so information might be lost. Protect your intellectual property and comply with the Privacy Act by only using Bond University recommended data storage solutions. Also see 'VI. If there are essential updates to the data, preserve a new version in addition to the old, but do not change the original version. +31 (0)30 253 35 50, Working safely with research data from home, Tools for storing and managing code and software, Online training 'Learn to write your DMP', Best Practices for Writing Reproducible Code, IT-solutions for storing and preserving data, The ins and outs of metadata and data documentation, Netherlands Code of Conduct for Research Integrity, Utrecht University Policy Framework for Research Data. Research data management done right dictates that storing research data must enable data sharing, easy findability and access when needed. It's best to put 'roles' (such as the data manager, supervisor, dean, principal investigator, etc.) University and Colleges work, Resources and support at Cambridge overview, University of Cambridge Research Data Management Policy Framework, University of Cambridge Research Data Management Policy Framework overview, Engaging Researchers in Good Data Management 2017 Conference, University of Cambridge Statement of Records Management Practice and Master Records Retention Schedule, How the University In the context of digital data, long-term preservation is the process of maintaining data over time so that they can still be found, understood, accessed and used in the future. It is tempting to keep everything, just in case you need it in the future, but keeping all your files for the foreseeable future costs money, and makes it more difficult to find the truly important things. Therefore, roles and responsibilities should be written down in an archival policy, making clear who is responsiblefor doing what withyour data in the long term. However, you may not be around during your whole research career to provide the appropriate care. Backup is well organised through our supplier SURFSara. This will help you find sets of files with a simple sorting of filenames in your folder. Choices are, for instance: What exactly to preservealso depends on your purpose: In both cases, enough documentation needs to be added to make the data comprehensible. We also have a support agreement with SURFSara and a processor agreement for the secure storage of personal data. Both can be used to describe the subject of the measurementsor the settings/circumstances under which these were obtained. In your day-to-day research make sure you manage the different versions and copies of your data carefully in the following ways: As your work progresses, it is likely that youll have more and more files, all with different content. ), you store one back-up in a different location from the others (to keep your files safe in case of a fire, flood, burglary, etc. How do you ensure that the data remains accessible when you or other people leave the research? As future access and reuse of data may be affected by proprietary formats, it is advisable to use open formats such as Rich Text Format (RTF) or Open Document Format (ODF) for preservation purposes. lab management software inventory future research Having the data available in a standard format after your research project ends will increase the possibilities for reuse. does my funder or the university need me to keep this data and / or make it available for a certain amount of time?
Portable storage media such as memory sticks (USB sticks) are more risky and vulnerable to loss and damage. For USB and CD/DVD, physical destruction works best to erase data. This way there is no conflict when the files are moved to another folder and you avoid working in the wrong file without realising it. Having a solution for preserving data for the long term can be pursued in several ways. For the UMC Utrecht Research Data Management policy, see the UMCU intranet page. Treat these as convenient working devices, but not as primary stores. IT professionals strongly recommend that: Your choice of storage media for back up will depend on the quantity and type of data you have: memory sticks, online back up services (i.e. Avoid using unsafe internet connections. 1. Overwrite the files to scramble their contentsor use secure erasing software. Migrating data from an unsuitable format to amore durable and accessibleone is usually difficult, expensive and may in some cases be impossible. CRICOS Provider Code 00017B | 2018 Bond University |. Your results are captured in data. You haveto prevent that someone can, willingly or not, overwrite your files, delete themor change theircontents. You can use a commercial solution, or ask Research Data Management Supportto set up an archive. If necessary, you can encode file name elements. Youve done the hard work of producing your research. Be consistent in the file naming of different versions, for example by adding the date (YYYY-MM-DD) in the file or the version number. To help you decide what to back up and when, think about which files you would need in order to re-create or restore in the case of loss and which data are crucial for your work? The folder 'Test Project' in Research Drive contains some useful documents such as the Quick Guide Research Drive and the guide documentation and folder structure. do I have the legal and intellectual property rights to keep and re-use this data? No matter which solution you use, the two golden rules of storage apply. via SURFfilesender); destroying data in a consistent and reliable manner when needed. The above guidelines for file names naturally also apply to the folder names. It makes the data easier to find and understand. As a researcher, you determine the strategy you want to follow when giving out file names. What a waste it would be if your work cannot be found by fellow researchers, right? Researchers need to ensure that their research data is secure and retrievable for long term use. This documentation helps to remain consistent and to continue to understand the strategy long after you have completed your research. The AVG/GPDRstates that personal data may not be kept longer than is necessary for thepurposes for which they were collected or for which they are used. Always go from generic to specific. Perhaps research and development departments of the private sector are also looking for your work. An extendedset could be anything others might find valuable. controlling access to restricted materials with encryption. File names can be automatically generated by software you use (e.g. Library Staff Directory. The result of this obsolescence means that it may no longer be possible to access the file, read the file or reuse the data, either entirely or partially. In addition, follow the recommendations in the University of Cambridge Statement of Records Management Practice and Master Records Retention Schedule). Research data and primary materials must be preserved. temporary copies/moving files e.g. On the one hand, activities related to storing the data and, on the other hand, activities related to organising the data. and meaningful file names. ), you use multiple different types of storage media or storage media from different manufacturers (to protect against multiple media failures, e.g. even if a document can still be opened with new software, it may be altered to a degree as to no longer be understandable or reliable for continued research, storage media may have been degraded, scratched or broken, especially if they are portable (e.g. They are very convenient though, and useful for: Nearly everyone who has experienced serious data loss did not think it would happen to them - but it does happen periodically. The followingcharacteristics will help to ensure access: AtDANSa distinction is madebetween preferred and acceptable formats for deposits for data preservation and data sharing. The results can be catastrophic for your research project, or for you personally. Keep a log file where you explain your coded elements, so outsiders, collaborators, supervisors, or yourself in a years time, will be able to crack the codes. A project folder in Research Drive can be requested via the iFrontoffice, tile 'Education support' and then the form 'Research Drive'. data backup and access are already well organised from the start. If you are handling personal or sensitive data then you should check the cloud option is compliant with any data protection rules the data are bound by. Build your file names from elements. Each individual researchershould ensure that their research data is regularly backed-up and stored securely for the life of the project and throughout the minimum retention period (see tablebelow). This short video illustrates the value of good data management and provides a few key best practices (from Digital Preservation Europe), StorageBackupLong-term storage and preservationSelection choosing what to keepSharing what, why and how to share dataDigital repositories a dedicated page where we provide detailed guidance on various data repositories.
arm storage netapp facility server data management gov Cloudstoroffers the following benefits for Bond researchers: Cloudstorisuseful forsharing of de-identifieddata sets. However, sharing data with others poses risks. can become faulty. Always save the raw data file and ensure that no further changes can be made to it (e.g. Back up can be time-consuming or expensive if your files take up a lot of space, or if you keep different files in different locations. Preservationcan be done on tape, disk, or via cloud storage.
Keep file names short. These types of storage solutions pose a risk of data loss if your data is not backed up. If files are to be shared in a shared filespace,standardised file-naming conventions areeven more important. The person who initiates the sharing of folders and files is responsible for ensuring the safe and appropriate sharing of data.
because storage costs money; storage requires effort / staff hours; storing massive amounts of data complicates finding and accessing the truly important files. Choosing the right way to store your data can help you work more flexibly, easily and quickly. A minimum set of documentation and metadata could be anything you need to interpret and evaluate the measurements. Research Drive offers the possibility to set up settings and authorisations in a way that complies with these conditions and applicable legislation [link naar interne vertaalde pagina]. The format is indicated by the file extensionat the end, such as .wmv, .mp3, or .pdf. data evolution database management hardware taking a presentation to a conference, files only one person at a time needs access to, whether files on the network are automatically backed up, and, if so, which folders or drives on the network are backed up automatically, you make two, or even three, back-ups of all important documents and data not stored on a networked file server (failure rates for storage media are probably higher than you think! save read-only or configure access rights). It is especially useful when you are working with several researchers on the same data. In order to keep research data secure, findable and readable, you, as a researcher, must carry out various activities. If applicable, the computer code used to perform analysesand/oranexplanation of performed analyses ('methods'); A file which describesthe files in the data package and their relation should be provided. This is up to you, the owner, to decide. If it is necessary to use your data outside Research Drive, apply encryption yourself using software such as VeraCrypt or Cryptomator. Any questions about Research Drive can also be asked via this form. storage research matrix data trobe infrastructure intranet provides required overview staff options login different You have two options: You shouldstore all your data and documentation filestogether in a data package. The software can ingest files, text, photos, provides for sharing where appropriate. The Bond Research Data Storeis available to all research staff and HDR students for day-to-day and long term data storage. These agreements must be included in the (joint) data management plan but also laid down in writing in a consortium agreement. Thoughtful storage solutions can also simplify version control and collaboration with others.
If the data is stored because it might be.
Elements could be project name, project number, name of research team/department,measurement type, subject, date of creation, version number, etc. It could also be a policy compliance matter. Moreover, when properly structured and annotated during research, youll have your data preserved and/or shared with minimal effort at the end of your research. data storage research management For short-term research projects that are for assessment purposes only, such as research projects completed by students, retaining research data for 12 months after the completion of the project may be sufficient; For most clinical trials, retaining research data for 15 years or more may be necessary; For areas such as gene therapy, research data must be retained permanently (e.g. It is therefore advisable not to have too many levels in the folder structure. However, there are points and rules you should keep in mind when making your choice: In summary, therefore, file names should contain useful clues as to the contents, status and version of the file. Software such as. Each element is coded to keep names short. All research data can be safely stored during the research using the Research Drive tool. data center google trends cloud infrastructure centers bringing future cxotoday vertiv shaping key utah tremendous undergoing facilities such change techcrunch data computing storage resources mcgill centre distributed users A range of different storage options are provided for University members by UIS. Make file names specific, detailed and unique. Ensure file names are independent of location (this will avoid problems when moving files). FTP servers) may be convenient for small amounts of data, whereas hard drives or magnetic tapes may be more appropriate for large volumes or when you need to store data offline for security reasons.
Do not use passwords on your universitycomputer only, but also on your laptop or home computer. Once you have accepted this, the functional administrator can make you owner of the project folder and the owner can then invite (research) staff to access Research Drive. Computing officers will not back them up or support them centrally. The Research Drive storage system uses encryption. Every day, researchers both inside and outside of your community, domain and country may be searching for research data that could help their own. It is also worth remembering that if you have something on file, then it might be subject to a Freedom of Information (FOI) request. Utrecht UniversityHeidelberglaan 83584 CS UtrechtThe NetherlandsTel. A decent firewall and reliable antivirus software are a must. Storing your data properly can save you a lot of time (in finding and interpreting) and frustration (in not losing it). There are roughly three goals to use specific types of metadata and data documentation: Your (raw) data may consist of several files with measurements (or interviews/observations/samples/etc.). Many computer networks within the University back up files automatically, but some do not. Will you only preserve the data underpinning a scientific publication, or also other data? For more information view theLabArchivesTutorials and Informationpage.
digital sources degrade over time ('bit rot'); data and software can become outdated. Make sure your folders and files are clearly structured and use informative This is not just for the sake of ensuring researchers in the future can make use of your outputs. Lock your computer when leaving it, even if it isjust for a moment (Windows key + L); Lock your door if you are not in your room; Do not leave unsecured copies of your data lying around; Transport your USB stick or external hard disk in such a way that you cannot lose it; Keep non-digital material which should not be seen by others, in a locked cabinet or drawer. The following elements can be used as a basis for file names: project name, project number, research team name, measurement type, subject, creation date, version number. All we can do is think the matter through carefully, abide by the policies we need to (e.g.
Ask A Librarian
Research Ethics Manager It is therefore important to store the data in a consistent manner and to provide accurate documentation and metadata. During data collection and analyses, researchers may select specific data formats. These following questions, based on material devised by the Digital Curation Centre, can help you decide what you should keep and what can be deleted: Once you have sorted through your files and asked these questions you then need to: Some funders require that all data is kept even if it is not publicly shared. For verification, all documentation and data (raw or possibly analysed) that enable research replication must be provided. It must allow reuse by others and protected against loss. questions, How the You can then simply refer to their storage. EUDAT publishes new use cases: CompBioMed, ROHub TNC22: EUDAT for NRENs and Research and Academia, Introduction to the EUDAT CDI and its Services. When using data from an external party, you must comply with the specific restrictions (e.g. See 'Tools for storing and managing data' for an overview of the tools Utrecht University has developed, supports and endorses. Youve invested a lot of time and effort in creating your data, so keep it safe.