The easiest and more efficient way to audit the same with Lepide Active Directory Auditor has also been explained. This article was written by Yuval Sinay, Microsoft MVP.  (For using with /Source 3 ). This is the search query I've managed to piece together.
(For using with /Source 3 ). This is the search query I've managed to piece together.
| convert timeformat="%m/%d/%y %H:%M:%S" ctime(_time) as Logontime The below filter attributes can be added or removed to the reports under the Local Logon-Logoff category using the Add / Remove Columns link. Click Apply and Ok.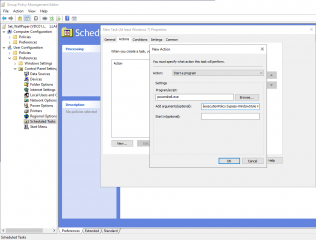 Windows Active Directory (AD) is important for coordinating security group managementacross servers, but doesnt offer all the features admins need. Get help, be heard by us and do your job better using our products.
Windows Active Directory (AD) is important for coordinating security group managementacross servers, but doesnt offer all the features admins need. Get help, be heard by us and do your job better using our products.
To audit successful and failed events, click both Successful and Failure checkboxes. Submit a ticket for technical and product assistance, or get customer service help. If you need to demonstrate compliancewith regulations like HIPAA, SOX, DISA STIG, or others, youll likely need to perform regular, thorough event log audits. A logon event audit consists of collecting and analyzing log data of user activity to create a report that highlights critical information about logon/logoff events. | table Logontime, Logofftime, SessionDuration, User, host Anyone have any ideas to try and make this work? Accelerates the identification and getting to the root cause of application performance issues.
Even with this you'll have some considerations, like if the user is remote & accessing the network via VPN, if you're trying to account for BYOD, etc. The session start time is displayed as Logged.
You can also search for these event IDs. Windows Active Directory is critical for configuring secure access to server data, but AD only goes so far in actively displaying and managing the activities of various users and groups. Hello everyone! Added browse button in the 'Advanced Options' window to choose the external folder. Currently, when I search this date range, it provides one metric of 99+ hours of session duration. logon borowski logoff auditing The issue I am finding is in our environment the logs only go back a couple of days. Into databases? You should turn on this option if you have Windows 10 with April Update (1803) and WinLogOnView stopped working. up. There are two types of auditing that address logging on, they are Audit Logon Events and Audit Account Logon Events. Subscription and Perpetual Licensing options available. If your server doesnt have Active Directory deployed, these policies can also be configured at the local machine. SaaS-based infrastructure and application performance monitoring, tracing, and custom metrics for hybrid and cloud-custom applications.
SaaS-based infrastructure and application performance monitoring, tracing, and custom metrics for hybrid and cloud-custom applications.
Privileged access management is a crucial security strategy that involves monitoring logon and logoff events to help reveal when a user is accessing data improperly and potentially posing a business risk. Clicking on an event in the bar graph, filters the report view highlighting only the selected event.
Help Reduce Insider Threat Risks with SolarWinds. | transaction User maxevents=2 startswith="EventCode=4624" endswith="EventCode=4634" maxspan=-1 Conducting logon audits can also help support improving the system security with better transparency into user access data. Users with greater access may be able to delete, modify, and even leak critical server data accidentally, or in the case with cyberattackers who gain these privileged user credentials through attacks like phishing, with malicious intent. If you want to get the logon/logoff information of a remote computer on your network, simply go to the Advanced Options window (F9), used in the 'About' window. reports member audit directory active windows server sample
Conducting logon audits can also help support improving the system security with better transparency into user access data. Users with greater access may be able to delete, modify, and even leak critical server data accidentally, or in the case with cyberattackers who gain these privileged user credentials through attacks like phishing, with malicious intent. If you want to get the logon/logoff information of a remote computer on your network, simply go to the Advanced Options window (F9), used in the 'About' window. reports member audit directory active windows server sample
All rights reserved. 12/11/17 20:00:29 12/11/17 20:00:29 0h 0m 0s john.doe PrimaryDC Network management tools, from configuration and traffic intelligence to performance monitoring and topology mapping, to readily see, understand, and resolve issues. https://answers.splunk.com/answers/127012/how-can-i-use-windows-events-to-monitor-logon-sessions.htm https://answers.splunk.com/answers/101366/collecting-logon-logoff-logs-from-active-directory-and-put BSides Splunk 2022 Call for Papers is Open Until August 12. That is a good feature to grab the local logins for laptop users for example. The best way to do this for this particular issue was to pull the logs from the client computer. hope it helps. And he never married Pocahontas.
Save the list of all logon sessions into HTML file (Horizontal).
data ivanti report query under ldms enter sure making right Go to Start All Programs Administrative Tools. I am trying to get out in front of my IT Department. Our budget and staffing, for our vertical. (Transportation).Smallish company, 90ish staff plus a large number of contractors. Busting at the edges and running towards technology as fast as we can. P Will raising password character requirements force people to change? WinLogOnView.exe /shtml "f:\temp\logon.html" /sort 2 /sort ~1 12/11/17 16:12:34 12/11/17 16:13:06 0h 0m 32s john.doe PrimaryDC. Comprehensive server and application management thats simple, interoperable, and customizable from systems, IPs, and VMs to containers and services. Close Group Policy Management Console. 12/11/17 20:43:03 12/11/17 20:43:14 0h 0m 11s john.doe PrimaryDC In order to change the language of
Platinum 2020 Best Security Incident & Event Management Solution (SIEM) SolarWinds Security Event Manager (SEM), SolarWinds uses cookies on its websites to make your online experience easier and better. Splunk, Splunk>, Turn Data Into Doing, Data-to-Everything, and D2E are trademarks or user layering citrix application layers logon sid machine indicates logoff diag name View SolarWinds Hybrid Cloud Observability Features, Server Performance & Configuration Bundle, Application Performance Optimization Pack, Web Application Monitoring & Performance Pack, IT Service AppOptics: Next-gen SaaS-based application performance & infrastructure monitoring. (Only when the 'Use New Event Log API' option is turned on), Fixed to display error on status bar when WinLogOnView fails to access the event log. Open Filter Current Log on the rightmost pane and set filters for the following Event IDs. Monitor, analyze, diagnose, and optimize database performance and data ops that drive your business-critical applications. The following article will help you to track users logon/logoff. To get the exact session time; you need to consider the very first logon and logoff time displayed in the event properties. Select the Period (between 1 hr and 23 hours), a custom period can also be defined & saved for easy reference. Network logons are logged for all kinds of activity, so you'll probably see dozens - even hundreds - of logon type 3 events throughout the day for each user. Are you aware of any free utilities that will let you gather logon/logoff information from a Windows domain controller and allow you to enter a date range and select just one user? SolarWinds SEM also includes an alert feature that can notify you about suspicious logon and logoff events, complete with automated security responsesto disable bad actors, so you can better mitigate and prevent potential cybersecurity breaches by detecting and addressing malicious activity before it happens. I know that there are events you can look for in the event viewer that can help indicate. The session end time (can be obtained using the Event ID 4647) is 11/24/2017 at 03:02 PM. If the user's computer is online when I run the search I can add their computer to the utility and it will gather the logs from their local computer too. You'll have to assemble a script yourself to query for your exact needs.. Yes, event 4626 is new in Windows 2012 and Windows 8 I believe. choose 'Remote Computer' as data source, and then type the name of the remote computer to connect. The only log you might be able to build somewhat reliable session information from is on the systems that the users log on to directly - it's WinEventLog://Microsoft-Windows-TerminalServices-LocalSessionManager/Operational but you'll need to collect it from all endpoints. Logging in (authenticating) is an event that can be tracked through the security logs, but logging out often can't be, and then you have the forced power downs, closing the laptop lid, etc. Run WinLogOnView with /savelangfile parameter: Open the created language file in Notepad or in any other text editor. logon session with a big THANK YOU. In this article, well discuss two methods for tracking user logon history; the native auditing method (Event Log) and an automated solution Lepide Active Directory Auditor (part of Lepide Data Security Platform). Save the list of all logon sessions into a comma-delimited text file (csv). It's possible that some of the information will be missing, like a logon session without logoff time. Compiling and sharing log data is a necessary requirement for many industry-specific security log audits.
I'll report back on what I find. I'll send you here to Ashleys blog entry: http://blogs.technet.com/b/ashleymcglone/archive/2014/10/29/microsoft-virtual-academy-using-powershe At the bottom is a link containing his scripts from the 8 hour MVA course., Have a look in the forensics section. I've kind of been curious about this kind of thing, though. assign quota logon logoff notification timeout customise The starting point to auditing logon events is collecting the logon and logoff data, typically located in a directory service like Windows Active Directory (AD) where admins can configure security groups, manage privileged user information like logon credentials, and specify who can modify server data. For example - You'll get authentication events all night if a user locks their system instead of logs off.
The parameter can specify the column index (0 for the first column, 1 for the second column, and so on) or For more information on cookies, see our, Monitoring and optimizing multiple DBMS platforms has never been simpler, Monitor, diagnose, and optimize SQL Server and Azure SQL, Database performance monitoring and optimization for traditional, open-source, and cloud-native databases, Easy-access, self-managed database documentation and data lineage analysis, Save time managing tedious data warehousing ELT/ETL tasks, Have complete monitoring and tuning control over your Microsoft SQL Server environment. To set the Windows audit policy, use Group Policy Object Editor or a similar application to define the default policy so it includes Success and Failure for audit process tracking. Web application performance monitoring from inside the firewall. Get insight into information like date, time, username, and activity. This is quite a rabbit hole. some great answers and queries from this portal: For logon audits, SEM has a number of useful out-of-the-box authentication reports that can list authentications tracked by SEM, such as user logon, logoff, failed logon attempts, guest logons, logons by monitored devices, and more. Close Group Policy Management Editor. After youve established your standards for monitoring logon events, SEM is built to provide industry-specific audit logs as well as live security alerts. Integrates with Dameware Remote Support and the Orion Platform. This tool is based on the security event log of Windows, and the accuracy of the displayed information depends on the availability and accuracy of the data stored inside the security event log. Optimize resource usage and reduce MTTR with powerful monitoring, discovery, dependency mapping, alerting, reporting, and capacity planning.
I realize the logoff information may not be reasonable but having the ability to know when a specific user connected to our network from date a to date b is what I am seeking. Fast and powerful hosted aggregation, analytics and visualization of terabytes of machine data across hybrid applications, cloud applications, and infrastructure.
logon currentware logoff Be aware that currently when using the 'Use New Event Log API' option, the loading process is slower than the old API mode. Cloud Based ITSM Application including Employee Service Management, Incident and Change Management and IT Asset Management. "s" I've seen several threads, but nothing to really dial in what we're needing for reporting.
Added option to choose another font (name and size) to display in the main window. When you specify this command-line option, the list will be saved without any sorting. Figured I would see if anyone else had input on this while I keep waiting on my ticket to be answered. https://answers.splunk.com/answers/462736/report-to-monitor-logonlogoff-time-and-duration-on.html the name of the column, like "User Name" and "Logon Time". This topic has been locked by an administrator and is no longer open for commenting.
Logon data is a central issue for identifying insider threats, since unusual logon events (and logoff events) can signal an anomaly in password-protected activity. Report for showing users logon / logoff and the duration. | search NOT (Account_Name=$ OR Account_Name=SYSTEM OR Account_Name=ANONYMOUS) Older systems are not supported because the log on/log off information is not added to the security event log. 12/11/17 16:28:28 12/11/17 16:38:41 0h 10m 13s john.doe PrimaryDC Enable Auditing on the domain level by using Group Policy: Computer Configuration/Windows Settings/Security Settings/Local Policies/Audit Policy. Perform the following steps in the Event Viewer to track session time: Lets use an example to get a better understanding. Double-click the event ID 4648 to access Event Properties. Thanks!
https://answers.splunk.com/answers/127012/how-can-i-use-windows-events-to-monitor-logon-sessions.htm
WinLogOnView, download the appropriate language zip file, extract the 'winlogonview_lng.ini', Be the first to know when your public or private applications are down, slow, or unresponsive. WinLogOnView now reads archive log files (Archive-Security-*.evtx) when using the external disk mode and local computer mode. However, even the best-trained cybersecurity specialist may not always be able to detect unusual logon events with their own eyes. | convert timeformat="%m/%d/%y %H:%M:%S" ctime(Logofftime) as Logofftime Translate all string entries to the desired language. If you want to get the logon/logoff information from external disk, simply choose 'External Disk' as data source and then type the https://answers.splunk.com/answers/511064/how-do-i-chart-windows-logon-and-logoff-per-user-b.html {Source Computer, Terminated Time, Message, Workstation Name, Logon Type, Logon Duration, Remarks, Client Host Name, Client IP Address, Radius Client IP Address, Radius Client Host Name, Event Type, Logoff Time, Logon Time, When, User Name, CALLER PROCESS NAME, Domain}, Privileges required for event log collection, Privileges required for automatic auditing configuration, Privileges required for file server auditing, Configuring Audit Policies for Active Directory Auditing, Configuring SACLs for Active Directory Auditing, Configuring Audit Policies for File Server Auditing, Configuring Audit Policies for Member Server Auditing, Configuring Audit Policies for Workstation Auditing, Configuring Audit Policies for NetApp Filer Auditing, Configuring SACLs for NetApp Filers Auditing, Configuring Audit Policies for NetApp Cluster Auditing, Migrating data between different versions of MS SQL, Moving ADAudit Plus from one server/drive to another, Migrating ADAudit Plus from 32-bit to 64-bit architecture. 12/11/17 18:14:29 12/11/17 18:14:29 0h 0m 0s john.doe PrimaryDC 12/11/17 23:32:29 12/11/17 23:32:29 0h 0m 0s john.doe PrimaryDC Find product guides, documentation, training, onboarding information, and support articles. Save the list of all logon sessions into a regular text file.
The 'Use New Event Log API' option is now turned on by default. Best I can offer, someone else might have pulled it together better. You can use it to gather those logs and run a Logon Sessions Report which should show you what you're looking for, provided the events are still in the Event Log. I found something called "eventcombMT" that does a good job at collecting the data but it doesn't do a good job at parsing it. Make sense of security log data more easily with SolarWinds Security Event Manager (SEM). ^^- this link helped me the most to begin with (as you can see from my search query). Azure SQL performance monitoring simplifed. You can put multiple /sort in the command-line if you want to sort by multiple columns. 12/11/17 16:28:29 12/11/17 16:29:01 0h 0m 32s john.doe PrimaryDC I think the data is in the security event logs of the domain controllers I was just hoping there was an easy to use free too that will collect and sort for me. Connect with more than 150,000+ community members. A logon (or logoff) event is an instance where a user logs into (or out) of a server. Keep track of logon data with an intuitive interface, Document audit logon events to demonstrate compliance, Detect unusual logon events and block them before its too late. SolarWinds Hybrid Cloud Observability. You may also be interested using LepideAuditor suite that helps to get historical logon/logoff reports into real time and filter the reports as per needs. logoff logon auditing 12/11/17 21:46:29 12/11/17 21:47:00 0h 0m 31s john.doe PrimaryDC You can save the log file as a .csv but here is some sample data it put in one cell (I masked the data between the brackets): "An account was logged off. Microsoft and/or its respective suppliers hereby disclaim all warranties and conditions with regard to this information and related graphics, including all implied warranties and conditions of merchantability, fitness for a particular purpose, workmanlike effort, title and non-infringement. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. But it gives me random times and only seems to pull information about the PrimaryDC. Subject: Security ID: S-1-5-[deleted] Account Name: [username] Account Domain: [OurDomain] Logon ID: [bunchofhexcharacters] Logon Type: 3 This event is generated when a logon session is destroyed. That is true to a point but when a user logs into their computer and it is connected to our domain, the domain controller that authenticated them adds the event to the security event log (on that DC) with Event ID 4626 for the logon. The Logon/Logoff reports generated by Lepide Active Directory Auditor mean that tracking user logon session time for single or multiple users is essentially an automated process. To simplify this. Fixed bug: WinLogOnView failed to display the logoff time even when there was 4647 event. A Pie / bar chart summarizes the actions in the selected domain. I shall lurk for a while. Optionally, you can also add your name and/or a link to your Web site.
Click here for instructions on how to enable JavaScript in your browser. WinLogOnView is also available in other languages. https://answers.splunk.com/answers/597752/report-for-showing-users-logon-logoff-and-the-dura.html, DLL Serach Oreder Hijacking (mitre : T1574.001), Search for disabled AD accounts that have been re-enabled. Integrates with Dameware Remote Everywhere and the Orion Platform.
Click on the Reports tab and select the Local Logon-Logoff tab on the left, to view the reports listing. Keep track of logon and logoff events with a centralized logon audit events monitor. ;). Be aware that WinLogOnView currently uses the following events: 4648 (Logon), 4647 (LogOff), 4624 (Logon), 4800 (Workstation lock). This activity will show up in the event logs, allowing admins to audit account logon events and gain visibility into logon activity. Monitoring and visualization of machine data from applications and infrastructure inside the firewall, extending the SolarWinds Orion platform. sourcetype="WinEventLog:Security" EventCode=4624 OR EventCode=4634 Account_Name=*
Manage and Audit Access Rights across your Infrastructure. | sort User host, Logontime Logofftime SessionDuration User host scripts logins Renew to download the latest product features, get 24/7 tech support, and access to instructor-led training. Management (ITSM), security information and event management (SIEM) software, Read more about SEM audit policy best practices. In the Group Policy Management console navigate to Forest Domains www.domain.com. Brand Representative for SystemTools Software Inc. Just keep in mind that tracking logOFF events might be nebulous at best.
I just wanted to start today's edition of the Snap! The first thing we need to do is increase the size of the security log files on all of our domain controllers. I have found some utilities that copy the log file data into it's own database so you can search for it beyond what your domain controllers store. Integrates with SolarWinds Web Help Desk, Basic On-Premises Remote Support software. (For using with /Source 2 ), Specifies the folder in external disk to load. logoff logon webgui If a logon event meets defined criteria, SEM is designed to be able to take immediate steps to protect the data and prevent additional user activityby disabling user accounts, logging off users, and blocking device IP addresses. Report for showing users logon / logoff and the du https://answers.splunk.com/answers/462736/report-to-monitor-logonlogoff-time-and-duration-on.html, https://answers.splunk.com/answers/511064/how-do-i-chart-windows-logon-and-logoff-per-user-b.html.
 (For using with /Source 3 ). This is the search query I've managed to piece together.
(For using with /Source 3 ). This is the search query I've managed to piece together. | convert timeformat="%m/%d/%y %H:%M:%S" ctime(_time) as Logontime The below filter attributes can be added or removed to the reports under the Local Logon-Logoff category using the Add / Remove Columns link. Click Apply and Ok.
 Windows Active Directory (AD) is important for coordinating security group managementacross servers, but doesnt offer all the features admins need. Get help, be heard by us and do your job better using our products.
Windows Active Directory (AD) is important for coordinating security group managementacross servers, but doesnt offer all the features admins need. Get help, be heard by us and do your job better using our products. To audit successful and failed events, click both Successful and Failure checkboxes. Submit a ticket for technical and product assistance, or get customer service help. If you need to demonstrate compliancewith regulations like HIPAA, SOX, DISA STIG, or others, youll likely need to perform regular, thorough event log audits. A logon event audit consists of collecting and analyzing log data of user activity to create a report that highlights critical information about logon/logoff events. | table Logontime, Logofftime, SessionDuration, User, host Anyone have any ideas to try and make this work? Accelerates the identification and getting to the root cause of application performance issues.
Even with this you'll have some considerations, like if the user is remote & accessing the network via VPN, if you're trying to account for BYOD, etc. The session start time is displayed as Logged.
You can also search for these event IDs. Windows Active Directory is critical for configuring secure access to server data, but AD only goes so far in actively displaying and managing the activities of various users and groups. Hello everyone! Added browse button in the 'Advanced Options' window to choose the external folder. Currently, when I search this date range, it provides one metric of 99+ hours of session duration. logon borowski logoff auditing The issue I am finding is in our environment the logs only go back a couple of days. Into databases? You should turn on this option if you have Windows 10 with April Update (1803) and WinLogOnView stopped working. up. There are two types of auditing that address logging on, they are Audit Logon Events and Audit Account Logon Events. Subscription and Perpetual Licensing options available. If your server doesnt have Active Directory deployed, these policies can also be configured at the local machine.
 SaaS-based infrastructure and application performance monitoring, tracing, and custom metrics for hybrid and cloud-custom applications.
SaaS-based infrastructure and application performance monitoring, tracing, and custom metrics for hybrid and cloud-custom applications. Privileged access management is a crucial security strategy that involves monitoring logon and logoff events to help reveal when a user is accessing data improperly and potentially posing a business risk. Clicking on an event in the bar graph, filters the report view highlighting only the selected event.
Help Reduce Insider Threat Risks with SolarWinds. | transaction User maxevents=2 startswith="EventCode=4624" endswith="EventCode=4634" maxspan=-1
 Conducting logon audits can also help support improving the system security with better transparency into user access data. Users with greater access may be able to delete, modify, and even leak critical server data accidentally, or in the case with cyberattackers who gain these privileged user credentials through attacks like phishing, with malicious intent. If you want to get the logon/logoff information of a remote computer on your network, simply go to the Advanced Options window (F9), used in the 'About' window. reports member audit directory active windows server sample
Conducting logon audits can also help support improving the system security with better transparency into user access data. Users with greater access may be able to delete, modify, and even leak critical server data accidentally, or in the case with cyberattackers who gain these privileged user credentials through attacks like phishing, with malicious intent. If you want to get the logon/logoff information of a remote computer on your network, simply go to the Advanced Options window (F9), used in the 'About' window. reports member audit directory active windows server sample All rights reserved. 12/11/17 20:00:29 12/11/17 20:00:29 0h 0m 0s john.doe PrimaryDC Network management tools, from configuration and traffic intelligence to performance monitoring and topology mapping, to readily see, understand, and resolve issues. https://answers.splunk.com/answers/127012/how-can-i-use-windows-events-to-monitor-logon-sessions.htm https://answers.splunk.com/answers/101366/collecting-logon-logoff-logs-from-active-directory-and-put BSides Splunk 2022 Call for Papers is Open Until August 12. That is a good feature to grab the local logins for laptop users for example. The best way to do this for this particular issue was to pull the logs from the client computer. hope it helps. And he never married Pocahontas.
Save the list of all logon sessions into HTML file (Horizontal).
data ivanti report query under ldms enter sure making right Go to Start All Programs Administrative Tools. I am trying to get out in front of my IT Department. Our budget and staffing, for our vertical. (Transportation).Smallish company, 90ish staff plus a large number of contractors. Busting at the edges and running towards technology as fast as we can. P Will raising password character requirements force people to change? WinLogOnView.exe /shtml "f:\temp\logon.html" /sort 2 /sort ~1 12/11/17 16:12:34 12/11/17 16:13:06 0h 0m 32s john.doe PrimaryDC. Comprehensive server and application management thats simple, interoperable, and customizable from systems, IPs, and VMs to containers and services. Close Group Policy Management Console. 12/11/17 20:43:03 12/11/17 20:43:14 0h 0m 11s john.doe PrimaryDC In order to change the language of
Platinum 2020 Best Security Incident & Event Management Solution (SIEM) SolarWinds Security Event Manager (SEM), SolarWinds uses cookies on its websites to make your online experience easier and better. Splunk, Splunk>, Turn Data Into Doing, Data-to-Everything, and D2E are trademarks or user layering citrix application layers logon sid machine indicates logoff diag name View SolarWinds Hybrid Cloud Observability Features, Server Performance & Configuration Bundle, Application Performance Optimization Pack, Web Application Monitoring & Performance Pack, IT Service AppOptics: Next-gen SaaS-based application performance & infrastructure monitoring. (Only when the 'Use New Event Log API' option is turned on), Fixed to display error on status bar when WinLogOnView fails to access the event log. Open Filter Current Log on the rightmost pane and set filters for the following Event IDs. Monitor, analyze, diagnose, and optimize database performance and data ops that drive your business-critical applications. The following article will help you to track users logon/logoff. To get the exact session time; you need to consider the very first logon and logoff time displayed in the event properties. Select the Period (between 1 hr and 23 hours), a custom period can also be defined & saved for easy reference. Network logons are logged for all kinds of activity, so you'll probably see dozens - even hundreds - of logon type 3 events throughout the day for each user. Are you aware of any free utilities that will let you gather logon/logoff information from a Windows domain controller and allow you to enter a date range and select just one user? SolarWinds SEM also includes an alert feature that can notify you about suspicious logon and logoff events, complete with automated security responsesto disable bad actors, so you can better mitigate and prevent potential cybersecurity breaches by detecting and addressing malicious activity before it happens. I know that there are events you can look for in the event viewer that can help indicate. The session end time (can be obtained using the Event ID 4647) is 11/24/2017 at 03:02 PM. If the user's computer is online when I run the search I can add their computer to the utility and it will gather the logs from their local computer too. You'll have to assemble a script yourself to query for your exact needs.. Yes, event 4626 is new in Windows 2012 and Windows 8 I believe. choose 'Remote Computer' as data source, and then type the name of the remote computer to connect. The only log you might be able to build somewhat reliable session information from is on the systems that the users log on to directly - it's WinEventLog://Microsoft-Windows-TerminalServices-LocalSessionManager/Operational but you'll need to collect it from all endpoints. Logging in (authenticating) is an event that can be tracked through the security logs, but logging out often can't be, and then you have the forced power downs, closing the laptop lid, etc. Run WinLogOnView with /savelangfile parameter: Open the created language file in Notepad or in any other text editor. logon session with a big THANK YOU. In this article, well discuss two methods for tracking user logon history; the native auditing method (Event Log) and an automated solution Lepide Active Directory Auditor (part of Lepide Data Security Platform). Save the list of all logon sessions into a comma-delimited text file (csv). It's possible that some of the information will be missing, like a logon session without logoff time. Compiling and sharing log data is a necessary requirement for many industry-specific security log audits.
I'll report back on what I find. I'll send you here to Ashleys blog entry: http://blogs.technet.com/b/ashleymcglone/archive/2014/10/29/microsoft-virtual-academy-using-powershe At the bottom is a link containing his scripts from the 8 hour MVA course., Have a look in the forensics section. I've kind of been curious about this kind of thing, though. assign quota logon logoff notification timeout customise The starting point to auditing logon events is collecting the logon and logoff data, typically located in a directory service like Windows Active Directory (AD) where admins can configure security groups, manage privileged user information like logon credentials, and specify who can modify server data. For example - You'll get authentication events all night if a user locks their system instead of logs off.
The
I realize the logoff information may not be reasonable but having the ability to know when a specific user connected to our network from date a to date b is what I am seeking. Fast and powerful hosted aggregation, analytics and visualization of terabytes of machine data across hybrid applications, cloud applications, and infrastructure.
logon currentware logoff Be aware that currently when using the 'Use New Event Log API' option, the loading process is slower than the old API mode. Cloud Based ITSM Application including Employee Service Management, Incident and Change Management and IT Asset Management. "s" I've seen several threads, but nothing to really dial in what we're needing for reporting.
Added option to choose another font (name and size) to display in the main window. When you specify this command-line option, the list will be saved without any sorting. Figured I would see if anyone else had input on this while I keep waiting on my ticket to be answered. https://answers.splunk.com/answers/462736/report-to-monitor-logonlogoff-time-and-duration-on.html the name of the column, like "User Name" and "Logon Time". This topic has been locked by an administrator and is no longer open for commenting.
Logon data is a central issue for identifying insider threats, since unusual logon events (and logoff events) can signal an anomaly in password-protected activity. Report for showing users logon / logoff and the duration. | search NOT (Account_Name=$ OR Account_Name=SYSTEM OR Account_Name=ANONYMOUS) Older systems are not supported because the log on/log off information is not added to the security event log. 12/11/17 16:28:28 12/11/17 16:38:41 0h 10m 13s john.doe PrimaryDC Enable Auditing on the domain level by using Group Policy: Computer Configuration/Windows Settings/Security Settings/Local Policies/Audit Policy. Perform the following steps in the Event Viewer to track session time: Lets use an example to get a better understanding. Double-click the event ID 4648 to access Event Properties. Thanks!
https://answers.splunk.com/answers/127012/how-can-i-use-windows-events-to-monitor-logon-sessions.htm
WinLogOnView, download the appropriate language zip file, extract the 'winlogonview_lng.ini', Be the first to know when your public or private applications are down, slow, or unresponsive. WinLogOnView now reads archive log files (Archive-Security-*.evtx) when using the external disk mode and local computer mode. However, even the best-trained cybersecurity specialist may not always be able to detect unusual logon events with their own eyes. | convert timeformat="%m/%d/%y %H:%M:%S" ctime(Logofftime) as Logofftime Translate all string entries to the desired language. If you want to get the logon/logoff information from external disk, simply choose 'External Disk' as data source and then type the https://answers.splunk.com/answers/511064/how-do-i-chart-windows-logon-and-logoff-per-user-b.html {Source Computer, Terminated Time, Message, Workstation Name, Logon Type, Logon Duration, Remarks, Client Host Name, Client IP Address, Radius Client IP Address, Radius Client Host Name, Event Type, Logoff Time, Logon Time, When, User Name, CALLER PROCESS NAME, Domain}, Privileges required for event log collection, Privileges required for automatic auditing configuration, Privileges required for file server auditing, Configuring Audit Policies for Active Directory Auditing, Configuring SACLs for Active Directory Auditing, Configuring Audit Policies for File Server Auditing, Configuring Audit Policies for Member Server Auditing, Configuring Audit Policies for Workstation Auditing, Configuring Audit Policies for NetApp Filer Auditing, Configuring SACLs for NetApp Filers Auditing, Configuring Audit Policies for NetApp Cluster Auditing, Migrating data between different versions of MS SQL, Moving ADAudit Plus from one server/drive to another, Migrating ADAudit Plus from 32-bit to 64-bit architecture. 12/11/17 18:14:29 12/11/17 18:14:29 0h 0m 0s john.doe PrimaryDC 12/11/17 23:32:29 12/11/17 23:32:29 0h 0m 0s john.doe PrimaryDC Find product guides, documentation, training, onboarding information, and support articles. Save the list of all logon sessions into a regular text file.
The 'Use New Event Log API' option is now turned on by default. Best I can offer, someone else might have pulled it together better. You can use it to gather those logs and run a Logon Sessions Report which should show you what you're looking for, provided the events are still in the Event Log. I found something called "eventcombMT" that does a good job at collecting the data but it doesn't do a good job at parsing it. Make sense of security log data more easily with SolarWinds Security Event Manager (SEM). ^^- this link helped me the most to begin with (as you can see from my search query). Azure SQL performance monitoring simplifed. You can put multiple /sort in the command-line if you want to sort by multiple columns. 12/11/17 16:28:29 12/11/17 16:29:01 0h 0m 32s john.doe PrimaryDC I think the data is in the security event logs of the domain controllers I was just hoping there was an easy to use free too that will collect and sort for me. Connect with more than 150,000+ community members. A logon (or logoff) event is an instance where a user logs into (or out) of a server. Keep track of logon data with an intuitive interface, Document audit logon events to demonstrate compliance, Detect unusual logon events and block them before its too late. SolarWinds Hybrid Cloud Observability. You may also be interested using LepideAuditor suite that helps to get historical logon/logoff reports into real time and filter the reports as per needs. logoff logon auditing 12/11/17 21:46:29 12/11/17 21:47:00 0h 0m 31s john.doe PrimaryDC You can save the log file as a .csv but here is some sample data it put in one cell (I masked the data between the brackets): "An account was logged off. Microsoft and/or its respective suppliers hereby disclaim all warranties and conditions with regard to this information and related graphics, including all implied warranties and conditions of merchantability, fitness for a particular purpose, workmanlike effort, title and non-infringement. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. But it gives me random times and only seems to pull information about the PrimaryDC. Subject: Security ID: S-1-5-[deleted] Account Name: [username] Account Domain: [OurDomain] Logon ID: [bunchofhexcharacters] Logon Type: 3 This event is generated when a logon session is destroyed. That is true to a point but when a user logs into their computer and it is connected to our domain, the domain controller that authenticated them adds the event to the security event log (on that DC) with Event ID 4626 for the logon. The Logon/Logoff reports generated by Lepide Active Directory Auditor mean that tracking user logon session time for single or multiple users is essentially an automated process. To simplify this. Fixed bug: WinLogOnView failed to display the logoff time even when there was 4647 event. A Pie / bar chart summarizes the actions in the selected domain. I shall lurk for a while. Optionally, you can also add your name and/or a link to your Web site.
Click here for instructions on how to enable JavaScript in your browser. WinLogOnView is also available in other languages. https://answers.splunk.com/answers/597752/report-for-showing-users-logon-logoff-and-the-dura.html, DLL Serach Oreder Hijacking (mitre : T1574.001), Search for disabled AD accounts that have been re-enabled. Integrates with Dameware Remote Everywhere and the Orion Platform.
Click on the Reports tab and select the Local Logon-Logoff tab on the left, to view the reports listing. Keep track of logon and logoff events with a centralized logon audit events monitor. ;). Be aware that WinLogOnView currently uses the following events: 4648 (Logon), 4647 (LogOff), 4624 (Logon), 4800 (Workstation lock). This activity will show up in the event logs, allowing admins to audit account logon events and gain visibility into logon activity. Monitoring and visualization of machine data from applications and infrastructure inside the firewall, extending the SolarWinds Orion platform. sourcetype="WinEventLog:Security" EventCode=4624 OR EventCode=4634 Account_Name=*
Manage and Audit Access Rights across your Infrastructure. | sort User host, Logontime Logofftime SessionDuration User host scripts logins Renew to download the latest product features, get 24/7 tech support, and access to instructor-led training. Management (ITSM), security information and event management (SIEM) software, Read more about SEM audit policy best practices. In the Group Policy Management console navigate to Forest Domains www.domain.com. Brand Representative for SystemTools Software Inc. Just keep in mind that tracking logOFF events might be nebulous at best.
I just wanted to start today's edition of the Snap! The first thing we need to do is increase the size of the security log files on all of our domain controllers. I have found some utilities that copy the log file data into it's own database so you can search for it beyond what your domain controllers store. Integrates with SolarWinds Web Help Desk, Basic On-Premises Remote Support software. (For using with /Source 2 ), Specifies the folder in external disk to load. logoff logon webgui If a logon event meets defined criteria, SEM is designed to be able to take immediate steps to protect the data and prevent additional user activityby disabling user accounts, logging off users, and blocking device IP addresses. Report for showing users logon / logoff and the du https://answers.splunk.com/answers/462736/report-to-monitor-logonlogoff-time-and-duration-on.html, https://answers.splunk.com/answers/511064/how-do-i-chart-windows-logon-and-logoff-per-user-b.html.